There are numerous reasons to be cautious of suspicious email in your inbox. Some messages might contain viruses or other malicious software while others can be phishing scams using copycat websites to steal personal information. Exercise caution and protect yourself by learning ways in which to handle what comes through your inbox.
But I have a spam filter, why is it not blocking these emails?
These emails are created by people who are dedicated to finding ways to explicitly bypass spam filters. Even though spam filters will block most spam, they are not perfect and these types of emails will occasionally get through as the spam filter finds a way to adapt and block them.
So in the meantime…
The best way to verify that an email is authentic is by looking at the sending email address as well as the email header. If the sender address does not match up with the Company name, it is usually spam. Spam can be greatly deceiving. There are ways for a fake email to show the sending address as a legitimate one, however, it can easily be faked. The one way to verify that the email is actually being sent from the real source is to check the email header as well.
If you receive an email that looks suspicious, another way to confirm its authenticity is by checking its links. However, we are not telling you to click directly on links or buttons you see because that could be harmful. Sometimes links can mask the actual website to which it links. Without clicking the link itself, you can hover over the link with your mouse and reveal the full URL of the link’s destination in the lower corner of the browser you’re using. Again, this is done without clicking on the link.
For Example:
Both of these links connect you to the Informatics home page, but you wouldn’t know that without using the hovering technique…
Contact Informatics for More Tech Tips
Click Here for a Free $100 GiftCard!
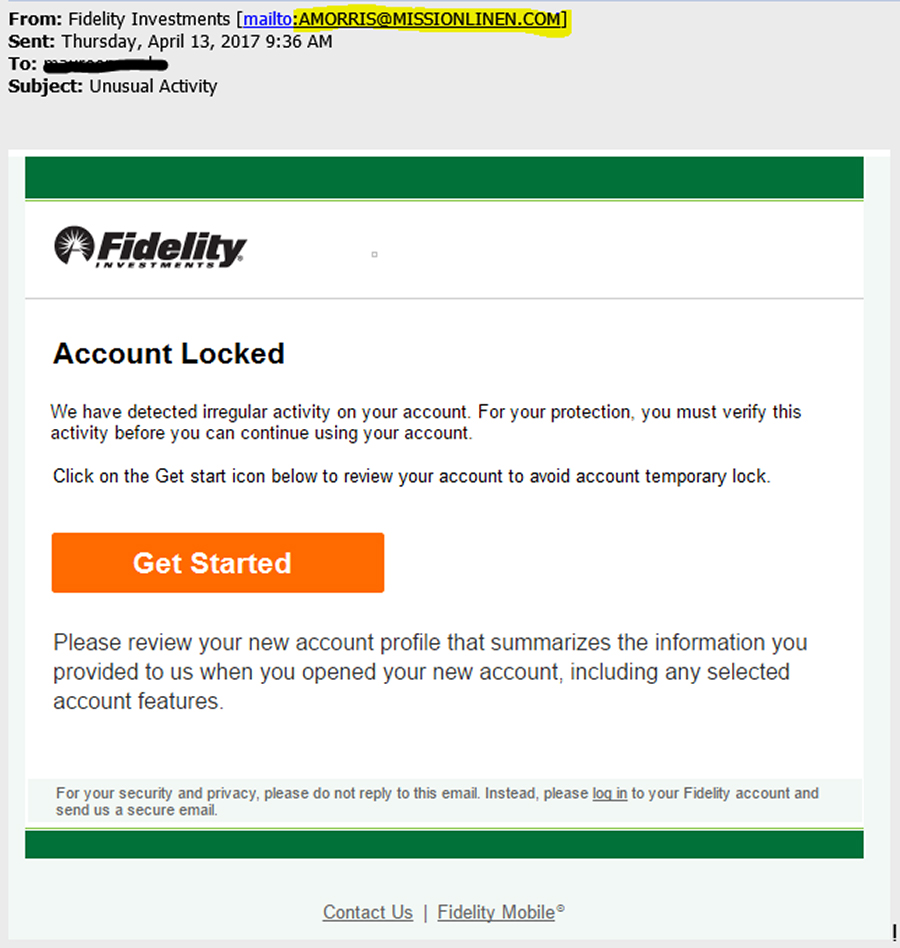
In the example below you can see that the seemingly harmless Get Started button does not link to the Fidelity Investments site. This is an email that is not actually from Fidelity Investments which means it should go directly to your trash box.
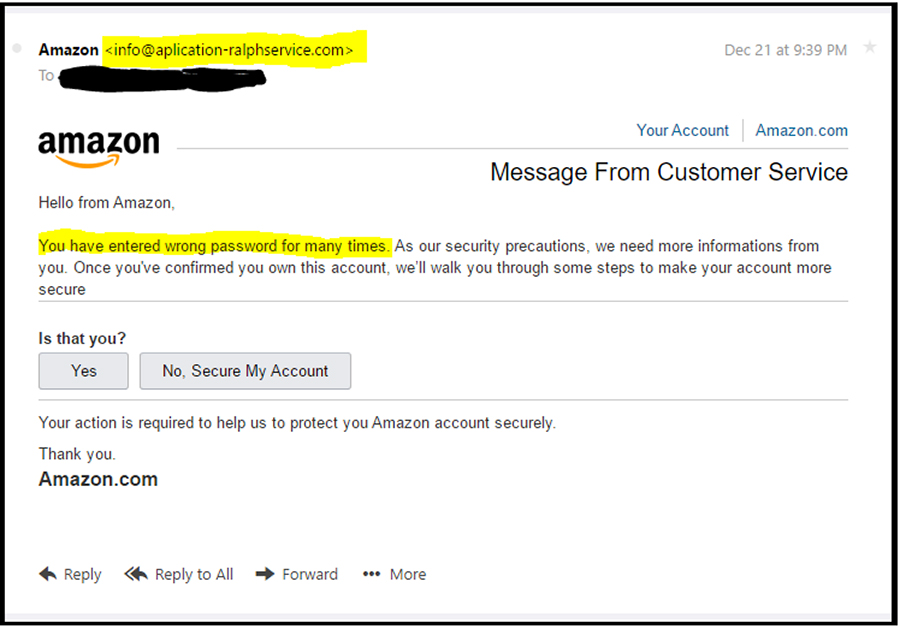
 You can also look at language in the email. The Amazon spam email below states: “You have entered wrong password for many times.” Many phishers also use fear to trigger a response. They will include messaging that make it seem urgent for a user to take action. These emails may claim that a failure to respond within a certain timeframe will result in account access being denied. Others may go so far as to claim that suspicious activity on a specific account has been detected.
You can also look at language in the email. The Amazon spam email below states: “You have entered wrong password for many times.” Many phishers also use fear to trigger a response. They will include messaging that make it seem urgent for a user to take action. These emails may claim that a failure to respond within a certain timeframe will result in account access being denied. Others may go so far as to claim that suspicious activity on a specific account has been detected.
Don’t be susceptible to attacks, always practice these tactics when receiving email that is even the least bit suspicious. Our tech team has expansive knowledge about online security and is always willing to help. If you have questions about suspicious online activity, take action and contact us today!
